Why It’s Time to Move Beyond VPN: The Shift to Zero Trust Network Access (ZTNA)

The remote-access model that secured yesterday’s networks can’t protect today’s hybrid, identity-driven world.
For more than two decades, Virtual Private Networks (VPNs) have been the backbone of remote work. They solved a very specific problem: give people outside the office a secure way to “join” the internal network. For a long time, that was good enough.
But the world changed. Work left the office. Applications moved to the cloud. Devices stopped being fully managed. And attackers stopped “breaking in” and started logging in with stolen credentials instead. In this new reality, VPN is not just a poor fit - it has become one of the most exploited weaknesses in the modern enterprise.
1. The VPN Problem You Can’t Ignore Anymore
VPN was designed for a world with a clear perimeter and a trusted internal network. Connect to the VPN and you became “inside”. That assumption breaks down completely in a hybrid, cloud-first, identity-centric environment.
1.1 VPN vs ZTNA at a Glance
| Capability | Traditional VPN | ZTNA (Zero Trust Network Access) |
|---|---|---|
| Access Level | Network-wide (subnets, hosts) | Application-specific |
| Trust Model | Trusted after login | Continuous verification (user, device, context) |
| Attack Surface | Exposed VPN gateways & ports | No exposed services, outbound-only connectors |
| BYOD Safety | High risk (no isolation) | Safe via isolated sessions |
| Cloud Performance | Backhauled, often slow | Direct, optimised for SaaS |
This table is the structural reason VPN is struggling: it was built around the network; ZTNA is built around identity, context, and applications.
1.2 Broad Network Access Becomes an Attacker’s Dream
A VPN tunnel doesn’t just connect a user to one application; it connects their device to an entire portion of your internal network. Once the tunnel is up, routing takes over. The user - or an attacker using their credentials - can now discover and talk to any reachable host on that network segment.
In a Zero Trust world, this is upside down. The goal is to give people exactly what they need and nothing more. VPN does the opposite: it gives them the network first, and the application is just one of many things they can now reach.
1.3 “Logged In” Still Equals “Trusted”
Modern attackers don’t spend most of their time hunting for exotic zero-days. They hunt for valid credentials: passwords reused across systems, leaked in breaches, harvested via phishing, or purchased on underground markets.
In a typical VPN setup, once a user’s credentials and MFA are bypassed or stolen, that’s it - there’s very little contextual intelligence to question the session. VPN does not natively ask:
- Is this device healthy and compliant?
- Is this login location suspicious for this user?
- Is this behaviour normal given their history?
- Should this session be allowed to reach this many systems?
It simply sees “credentials accepted” and opens the tunnel. That’s no longer compatible with how identity attacks work today.
1.4 A Simple VPN Attack Path
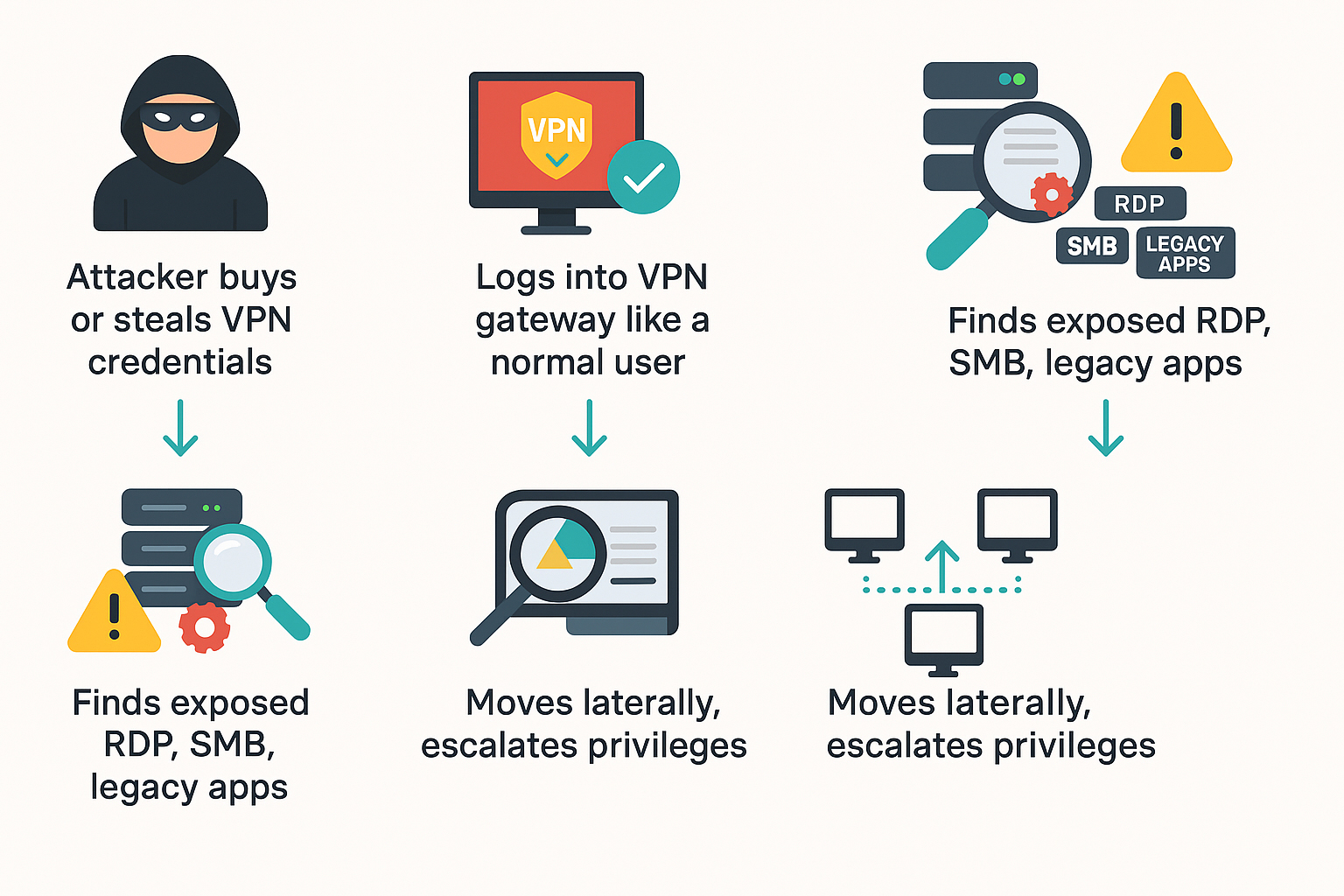
At no point did the attacker need to exploit a software bug - they only had to exploit a trust model.
1.5 BYOD and Contractor Devices: The Hidden Risk

As remote work accelerated, so did the number of unmanaged devices: personal laptops, contractor machines, offshore teams, temporary workers. With VPN, once these devices authenticate, they are treated like any other endpoint on the internal network, regardless of their security posture.
If a personal laptop is infected with a keylogger, infostealer, or remote-access trojan, the VPN connection becomes a bridge for that malware into the heart of your environment. VPN has no built-in way to isolate or sandbox those sessions.
1.6 Performance and Operational Pain
VPN also introduces very practical problems:
- Backhauling cloud and SaaS traffic through central gateways
- Latency, jitter, and dropped sessions, especially for remote workers
- Heavy reliance on client software and complex configurations
- Continuous patching, certificate management, and troubleshooting
VPN becomes a single choke point for traffic and a constant source of support tickets.
2. Why Organisations Are Moving to ZTNA
Zero Trust Network Access (ZTNA) is not just a “better VPN”. It’s a fundamentally different model: instead of extending the network to the user, ZTNA provides secure, conditional access to specific applications - based on identity, device posture, and context.
Network-centric (VPN)
- User joins the internal network
- Access controlled by IP ranges and firewalls
- Lateral movement possible
- BYOD is hard to trust
Identity-centric (ZTNA)
- User connects to a specific app
- Access controlled by policy, identity, and context
- Lateral movement is blocked by design
- BYOD can be safe via isolation
2.1 No Network Exposure
In ZTNA, internal apps are not exposed directly to the internet. There are no open ports to scan, no VPN login pages to brute-force, and no externally visible gateways advertising where your sensitive systems live.
ZTNA connectors typically initiate outbound connections from inside your network to the cloud control plane, which then brokers user access. To an attacker, those applications simply do not exist.
2.2 Identity, Device & Context Drive Every Decision
ZTNA evaluates each access request using multiple signals:
- Identity – Who is the user and what role do they have?
- Device – Is the device managed, healthy, and compliant?
- Location & behaviour – Is this login time, IP, and pattern normal for this user?
- Risk score – Are there indicators that this session may be compromised?
Access to an application is only granted if the combination of these factors meets policy requirements. This is very different from VPN’s single “password + token = tunnel” decision.
2.3 Application-Level Access, Not Network Tunnels
ZTNA narrows access from “the network” down to “this specific internal CRM”, “this admin portal”, or “this developer tool”. The user never sees the underlying subnets or infrastructure. They simply authenticate and are presented with the applications their role allows.
Visual: Network vs. Application Access
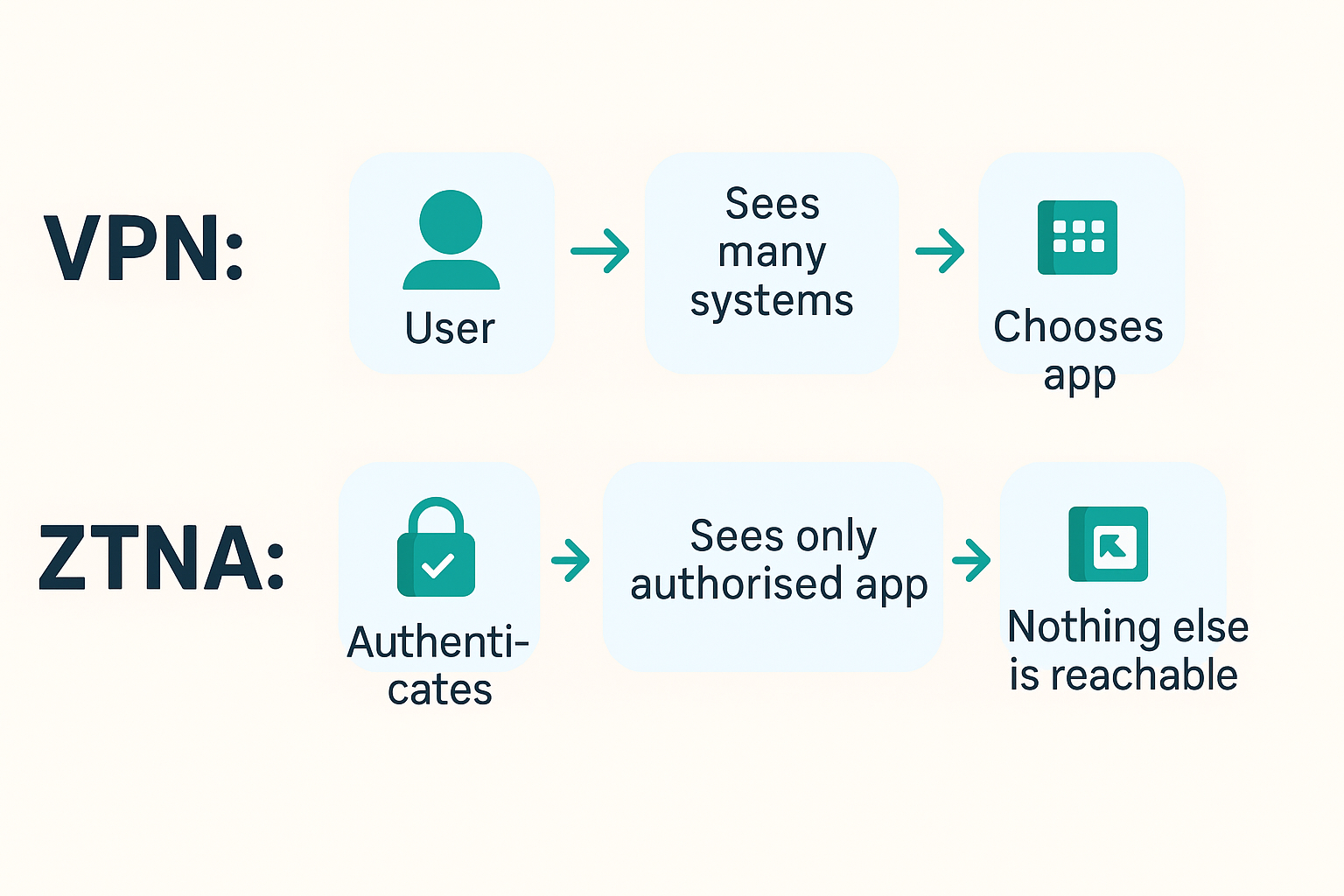
Shrinking the “blast radius” of any compromised account is one of the biggest practical advantages of ZTNA.
2.4 Isolation for Safer BYOD and Contractors
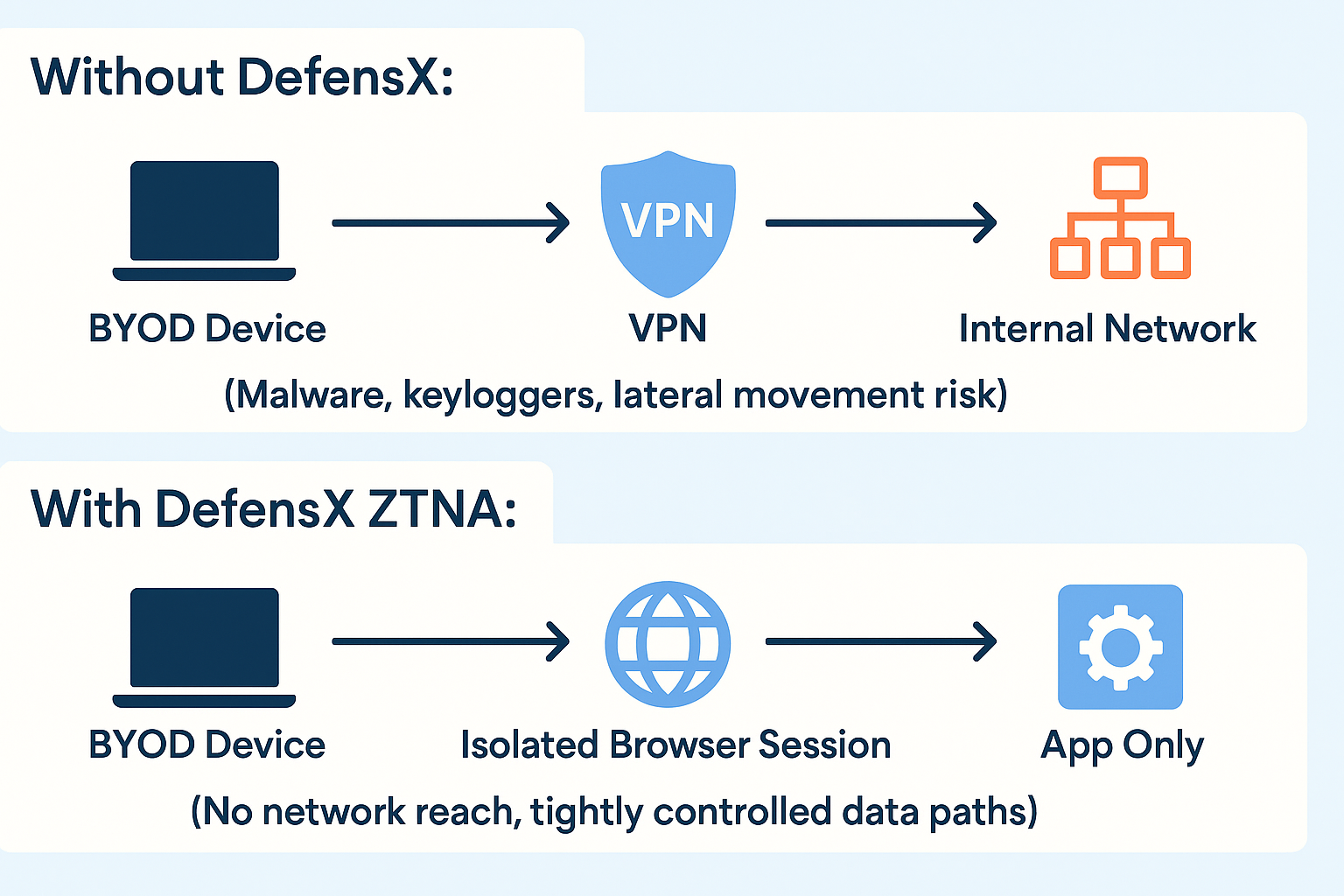
Many ZTNA implementations add another crucial layer: session isolation. Instead of letting unmanaged devices talk directly to internal services, they render the application in an isolated environment (often at the browser level), sending only pixels and controlled interactions back to the user.
This means a compromised device cannot easily infect internal systems, and sensitive data is much harder to steal via copy/paste, local file access, or screen scraping.
2.5 Cloud-Native Performance and Simpler Operations
ZTNA is designed for a world where most apps are already on the internet. Rather than backhauling SaaS and cloud access through a VPN gateway, ZTNA can route traffic directly - enforcing policy at the edge or in the browser.
This tends to:
- Reduce latency and improve responsiveness
- Remove single points of congestion
- Decrease the number of support tickets
- Simplify architecture and maintenance
3. From VPN to ZTNA: A Practical Migration Pattern
Moving away from VPN doesn’t need to be a disruptive “big bang” change. Most organisations follow a phased migration that reduces risk while gradually shrinking their VPN footprint.
Identify which apps, ports, and user groups rely on VPN today: internal web portals, RDP, SSH, file shares, admin tools, and so on.
Target high-risk, high-value systems first (admin consoles, finance, core business systems) and move them behind ZTNA.
Enforce stricter requirements for unmanaged devices and external users; apply lighter controls for known, compliant endpoints.
For especially sensitive access, enable browser-level isolation and granular control of downloads, printing, and screenshots.
As app coverage grows in ZTNA, remove corresponding VPN profiles until only legacy exceptions remain - then decommission VPN.
4. DefensX ZTNA: Zero Trust Built Directly Into the Browser
Most ZTNA products solve the network problem, but they stop at the edge. The real work, however, happens in the browser - where users interact with SaaS, internal web apps, admin panels, files, and AI tools all day long.
DefensX takes a different approach: it embeds ZTNA and Zero-Trust controls directly into the browser workspace itself, turning any tab into a secure, isolated, policy-driven environment.
4.1 Browser-Native Zero Trust (No Client, No Tunnel, No VDI)
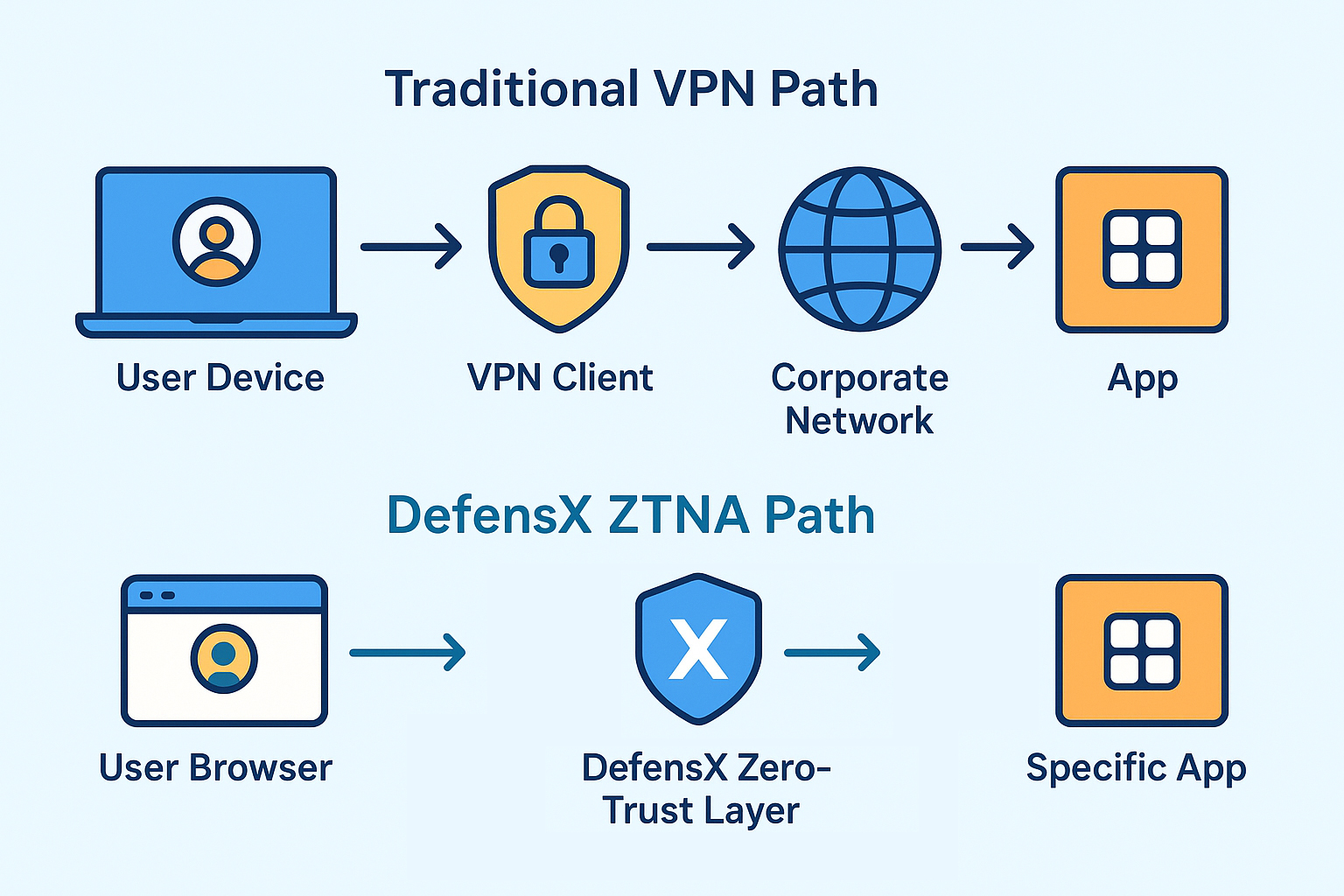
Users work in the tools they already know (Chrome, Edge, etc.), while DefensX quietly enforces Zero-Trust policies on every session.
4.2 Outbound-Only, Invisible to Attackers
DefensX ZTNA uses outbound-only connectors from your environment. There are no public VPN gateways, no externally visible RDP endpoints, and no open ports advertising where your critical systems live.
| VPN | DefensX ZTNA | |
|---|---|---|
| Inbound Exposure | Yes – gateways exposed to internet | No – outbound connectors only |
| Scan / Enumeration | Possible | Not discoverable |
| Public Login Surface | VPN portals, RDP behind VPN | None – access brokered via identity |
4.3 Session Isolation at the Browser Layer
Every DefensX ZTNA session runs inside an isolated browser container. That isolation protects both sides of the connection:
- Malware on the user’s device can’t directly reach internal apps
- Internal data is shielded from uncontrolled clipboard, print, and download actions
- Screen capture and other leakable paths can be governed or blocked
- BYOD and contractor devices can safely access sensitive apps
4.4 Visual: Isolated Sessions for BYOD
4.5 AI-Powered Protection Built Into Every Session
DefensX doesn’t stop at access. It also understands how users behave once they’re connected, and applies AI-driven protections where VPN and classic ZTNA are blind:
- Multi-layer phishing detection and response
- Controls around where and when credentials can be entered
- Browser-native DLP for files, PII, copy/paste, and screenshots
- Inspection and redaction of sensitive data in AI prompts
- Noise injection against keyloggers during sensitive input
- Defences against session hijacking and token theft
4.6 App-Level Access, Zero Lateral Movement
With DefensX ZTNA, users never “join” the internal network. They are granted a governed session into a specific application or resource. There is nothing to pivot to, no network to scan, and no internal IP ranges to explore.
VPN
- Network-wide reach after login
- Internal IPs exposed to authenticated users
- Lateral movement possible by design
DefensX ZTNA
- Only authorised app is reachable
- No visibility into underlying network
- Lateral movement structurally blocked
4.7 Built for Real-World Work: BYOD, Contractors, Distributed Teams
Because DefensX operates directly in the browser and uses isolation by default, it’s especially well suited for:
- Contractors and partners who should never have full network access
- Remote teams working from unmanaged or personal devices
- Developers and admins accessing internal tools from multiple environments
- Knowledge workers moving constantly between internal apps, SaaS, and AI tools
In all of those scenarios, DefensX ZTNA gives them what they need - fast, familiar access - without inheriting the risk their devices normally introduce.
5. Conclusion: VPN Had Its Era - But That Era Is Over
VPN solved a very real problem in a very different world. When work mostly happened inside the office, on managed machines, in a clearly defined network, extending that network outward via a secure tunnel made sense.
That’s not how modern organisations operate anymore. Today:
- Work is hybrid and global
- Devices are often unmanaged
- Applications live in the cloud
- Attackers target identities, not just infrastructure
- Zero Trust, not perimeter trust, is the security baseline
In this reality, VPN introduces more risk and friction than value. It exposes gateways to the internet, grants broad network access, struggles with BYOD, and often becomes the first step in a ransomware incident.
ZTNA - especially when delivered natively in the browser as DefensX does - offers a different path: application-specific, context-aware, fully isolated access that is invisible to attackers and intuitive for users.
The real question for most organisations is no longer “Should we move beyond VPN?”
It’s “How quickly can we transition to ZTNA without disrupting the business?”
The good news: with the right approach and a browser-centric Zero Trust platform, that transition can be both smooth and transformative - reducing attack surface, simplifying operations, and giving your users a remote-access experience that finally matches the way they actually work.

