Ready to enhance your data security strategy?
Contact DefensX today to learn how AI-powered web DLP can protect your business!
Use Cases
Working from home (WFH) creates enormous challenges for the user and the organization as ransomware and phishing attacks continue to grow.
Almost 550,000 URLs are created every day in addition to those that exist. 40% of malicious URLs are found in good domains. Attackers embed malicious scripts and applications into web pages:
Attackers can attack users in 9 out of 10 web applications. Attacks include redirecting users to an attacker-controlled resource, stealing credentials in phishing attacks, and infecting computers & mobile phones with malware/ransomware.
Zero-day threats are weaknesses that are exploited by attackers and undetected by affected parties. When an organization realizes they have been compromised, the intelligence tools they are using requires time to understand and respond to the attack.
In most cases, adversaries try to inject malware/ransomware by using drive-by-downloads, injecting a single line of code, or using other technologies.
DefensX applies user-friendly web protection technologies such as threat intelligence and whitelisting, based on the URL risk score so malware/ransomware won’t reach the endpoints.
DefensX’s solution is a plugin installed in the end users’ browser or an application installed in the end users’ mobile device (IOS/Android).
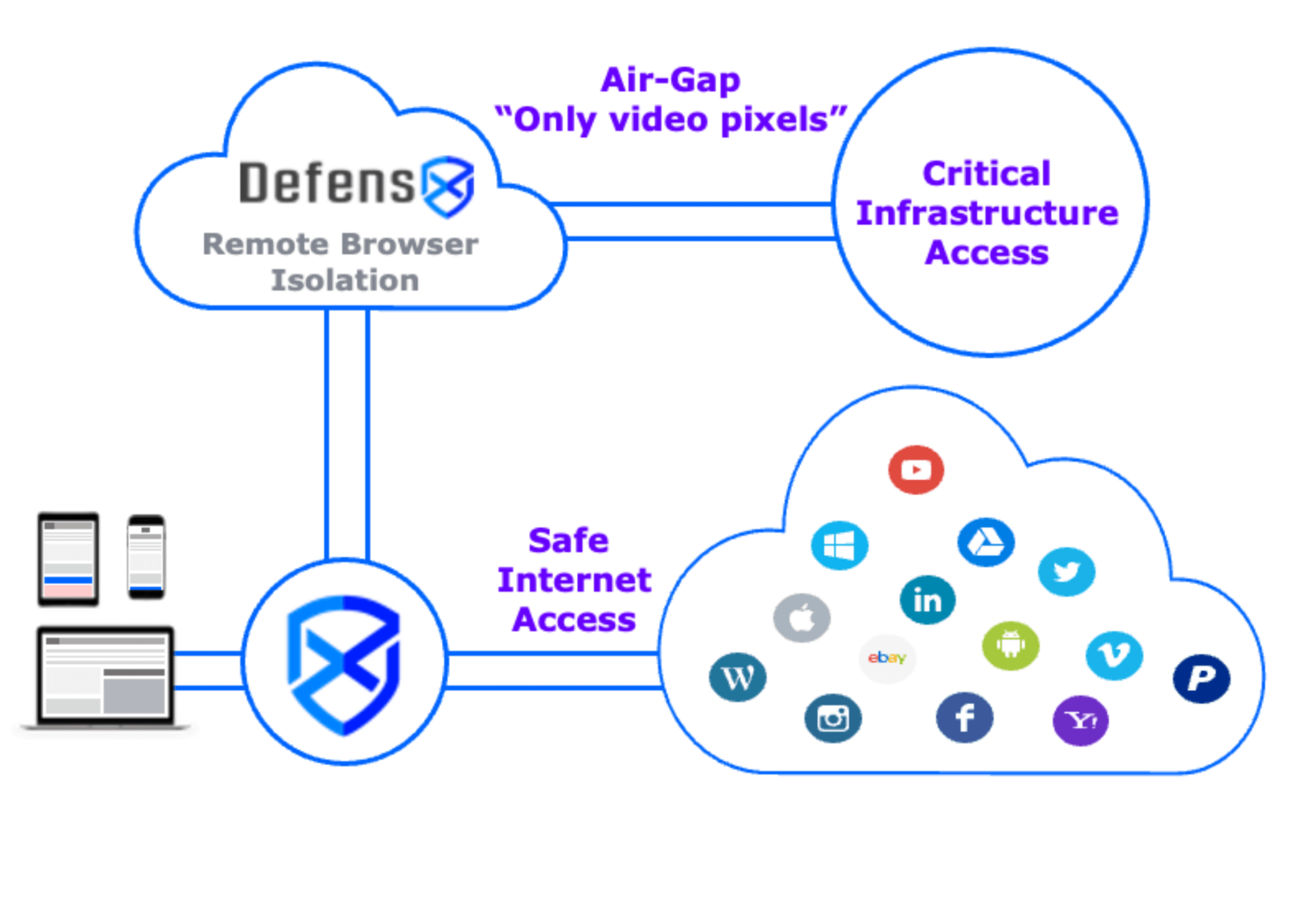
Remote Browser Isolation (RBI) is a cybersecurity model which aims to physically isolate an internet user's browsing activity, and the associated cyber risks, away from their local networks and infrastructure. The defined session is executed on the cloud, in a disposable container and the rendered image of the visited page is sent back to the end users’ browser. RBI is the most secure threat isolation technology that currently exists.
DefensX is cloud native – it is the first policy enforcer of an application without the need to send traffic to a SWG or CASB.
Policies are applied to the applications rather than the network layer. The content is inspected, and policies are defined before the traffic is encrypted. With DefensX, web traffic from cloud to end user remains unmodified.
DefensX’s local isolation protects end users with a security layer between the end user and the website.
DefensX combines end-user consent, company policies, and threat intelligence to create a personalized cybersecurity posture by leveraging end users’ daily web experience. This unique approach increases cyber awareness, adoption of cyber practices and dramatically reduces the load on cybersecurity professionals.
Contact DefensX today to learn how AI-powered web DLP can protect your business!